Provisioning Operators using an LDAP Server
ARM allows using the enterprise's LDAP server for operator login authentication. This feature is in addition to local operator login authentication described under Manually Provisioning an Operator in the ARM's Operators Page.
| ➢ | To add an LDAP operator login authentication server: |
| 1. | Open the LDAP Authentication Server page (Settings > Administration > LDAP Authentication). |
LDAP Authentication Server
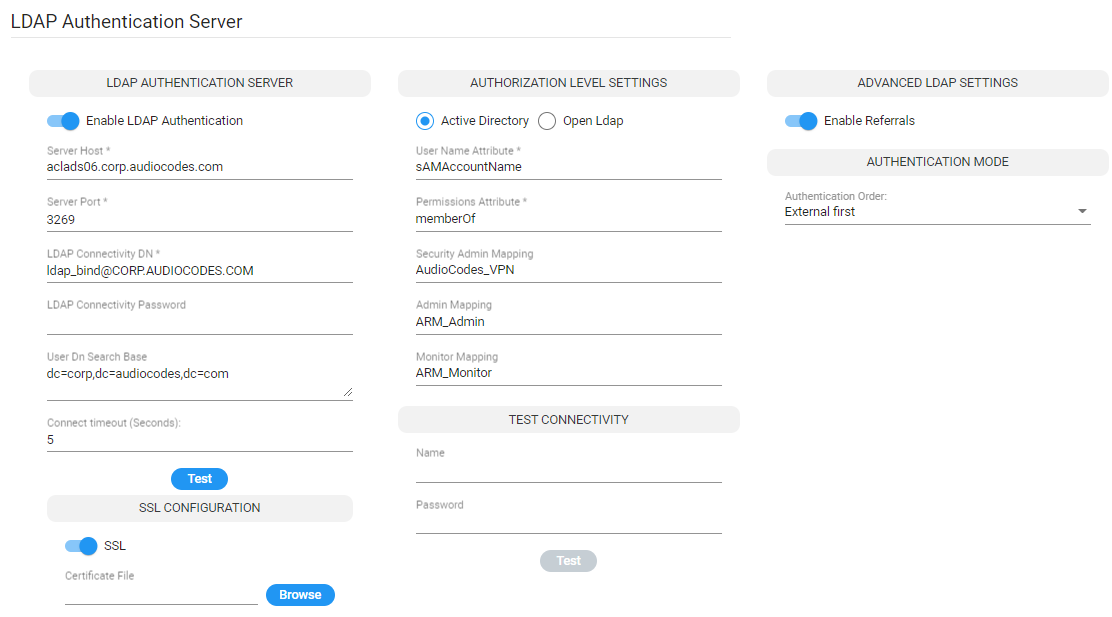
Only operators with a security level of Admin can edit LDAP authentication server parameters.
| 2. | Configure the LDAP Authentication Server parameters using the following table as reference. |
LDAP Authentication Server Parameters
| Parameter | Description |
|---|---|
|
Enable LDAP Authentication |
Switch this option on or off to enable or disable operator login authentication using an LDAP-compliant authentication server. |
|
Server Host |
Enter the IP address of the LDAP server's host. |
|
Server Port |
Enter the LDAP server's port number. Default: 389 |
|
LDAP Connectivity DN |
Configure the 'LDAP Connectivity DN' parameter as required. |
|
LDAP Connectivity Password |
Configure the 'LDAP Connectivity Password' as required. |
|
User DN Search Base |
Configure the 'User DN Search Base' as required. |
|
Connect timeout (seconds) |
Configure the operator login authentication timeout. Default: 5 seconds. |
|
Test |
This button tests the LDAP server; it tests whether you can connect to it with the bind user, whether the port is correct, etc. |
| 3. | Configure the SSL parameters to secure the connection to the LDAP server, using the following table as reference. |
SSL Parameters
| Parameter | Description |
|---|---|
|
SSL |
Enable the 'SSL' option to secure the connection with the LDAP server over SSL. If disabled, the connection with the LDAP server will be non-secured. |
|
Certificate file |
Click the Browse button to browse to and select the certificate file that you want to use to secure the connection with the LDAP server over SSL. If SSL is selected and a certificate is also selected, an HTTPS connection between the ARM and the LDAP server will be opened. The ARM authenticates the SSL connection using the certificate. |
| 4. | Configure the Test Connectivity parameters to test the connection to the LDAP server. Use the following table as reference. |
Test Connectivity
| Parameter | Description |
|---|---|
|
Name |
If 'Name' is undefined (empty), the connectivity test checks if the LDAP authentication server can be logged into per the values defined under the 'LDAP Authentication Server' parameters. If you enter a user name, the connectivity test checks that it's valid for logging into the ARM. Enter the user name assigned to the LDAP server. |
|
Password |
If 'Password' is undefined (empty), the connectivity test checks if the LDAP authentication server can be logged into per the values defined under the 'LDAP Authentication Server' parameters. If you enter a user password, the connectivity test checks that it's valid for logging into the ARM. Enter the password required for accessing the LDAP server. |
|
Test |
Click this button to test whether the user and the user's password have authorization. If the user matches the mappings on the right side of the screen, it will also 'test' the connection to the server itself. |
LDAP Connectivity Test Result
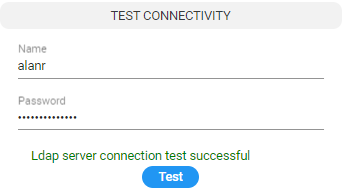
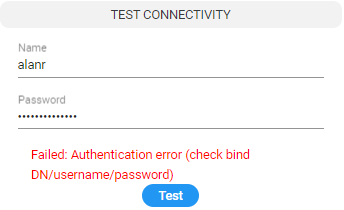
| 5. | View the result of the LDAP server connectivity test; the figure at left shows a successful connection while the figure at right shows a failed test. |
| 6. | Under page section 'Authorization Level Settings', you can provide mapping of the ARM's access rules (‘Security Admin’ and ‘Admin’) into the LDAP server’s values. Use the following table as reference. |
Authorization Level Settings
| Parameter | Description |
|---|---|
|
User Name Attribute |
The name of the LDAP-complaint server's directory | folder in which the enterprise's user names are located. Default: sAMAccountName. When the operator logs in, the authentication feature checks in this directory | folder that the operator's name exists. |
|
Permissions Attribute |
The name of the LDAP-complaint server's directory | folder in which the permissions are located. Default: memberOf. When the operator logs in, the authentication feature checks in this directory | folder if they have permission to log in. |
|
Security Admin Mapping |
The name of the LDAP-complaint server's directory | folder in which the ARM's access rule is mapped. Default: ARM_SecurityAdmin. When the operator logs in, the authentication feature checks against this directory | folder if login is allowed or not. |
|
Admin Mapping |
The name of the LDAP-complaint server's directory | folder in which the ARM's access rule is mapped. Default: Default: ARM_Admin. When the operator logs in, the authentication feature checks against this directory | folder if login is allowed or not. |
If LDAP authentication is enabled, the order used to authenticate operator login is:
| ● | LDAP |
| ● | Local storage (Database) |
If the LDAP server is down or if the operator can't be authenticated with the LDAP server because either the operator isn't found or the password doesn't match, the local operators table is used.
| 7. | Click Submit. |