Assigning IDS Policies
The IDS Matches table lets you implement your configured IDS Policies. You do this by assigning IDS Policies to any, or a combination of the following configuration entities:
| ■ | SIP Interface: For detection of malicious attacks on specific SIP Interface(s). To configure SIP Interfaces, see Configuring SIP Interfaces. |
| ■ | Proxy Sets: For detection of malicious attacks from specified Proxy Set(s). To configure Proxy Sets, see Configuring Proxy Sets. |
| ■ | Subnet addresses: For detection of malicious attacks from specified subnet addresses. |
You can configure up to 20 IDS Policy-Matching rules.
The following procedure describes how to configure the IDS Match table through the Web interface. You can also configure it through ini file [IDSMatch] or CLI (configure voip > ids match).
| ➢ | To configure an IDS Policy-Matching rule: |
| 1. | Open the IDS Matches table (Setup menu > Signaling & Media tab > Intrusion Detection folder > IDS Matches). |
| 2. | Click New; the following dialog box appears: |
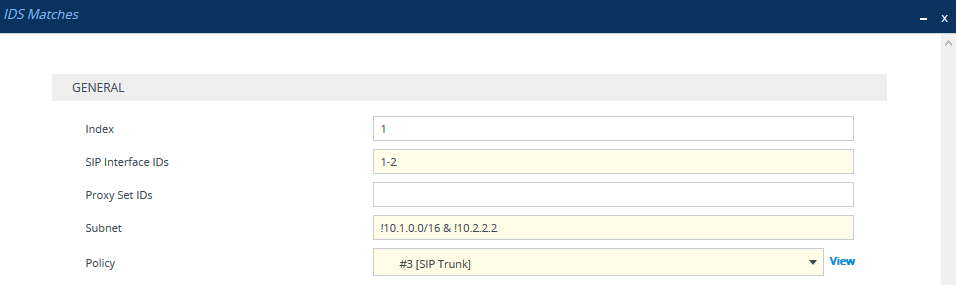
The figure above shows a configuration example where the IDS Policy "SIP Trunk" is applied to SIP Interfaces 1 and 2, and to all source IP addresses outside of subnet 10.1.0.0/16 and IP address 10.2.2.2.
| 3. | Configure a rule according to the parameters described in the table below. |
| 4. | Click Apply, and then save your settings to flash memory. |
IDS Matches Table Parameter Descriptions
|
Parameter |
Description |
|||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
'Index' [Index] |
Defines an index number for the new table record. |
|||||||||||||||||||||
|
'SIP Interface IDs' sip-interface [SIPInterface] |
Assigns a SIP Interface(s) to the IDS Policy. This indicates the SIP Interfaces that are being attacked. The valid value is the ID of the SIP Interface. The following syntax is supported:
|
|||||||||||||||||||||
|
'Proxy Set IDs' proxy-set [ProxySet] |
Assigns a Proxy Set(s) to the IDS Policy. This indicates the Proxy Sets from where the attacks are coming from. The following syntax is supported:
Note:
|
|||||||||||||||||||||
|
'Subnet' subnet [Subnet] |
Defines the subnet to which the IDS Policy is assigned. This indicates the subnets from where the attacks are coming from. The following syntax can be used:
|
|||||||||||||||||||||
|
'Policy' policy [Policy] |
Assigns an IDS Policy (configured in Configuring IDS Policies). |