Security Threats
AudioCodes devices are commonly located at the demarcation point between safe (trusted) and unsafe (untrusted) networks. A typical example of an un-trusted network would be a SIP trunk connected to an Internet Telephony Service Provider (ITSP) network; the trusted network would be the internal LAN. The following figure illustrates this basic concept of trusted and untrusted networks.
Trusted and Untrusted Networks
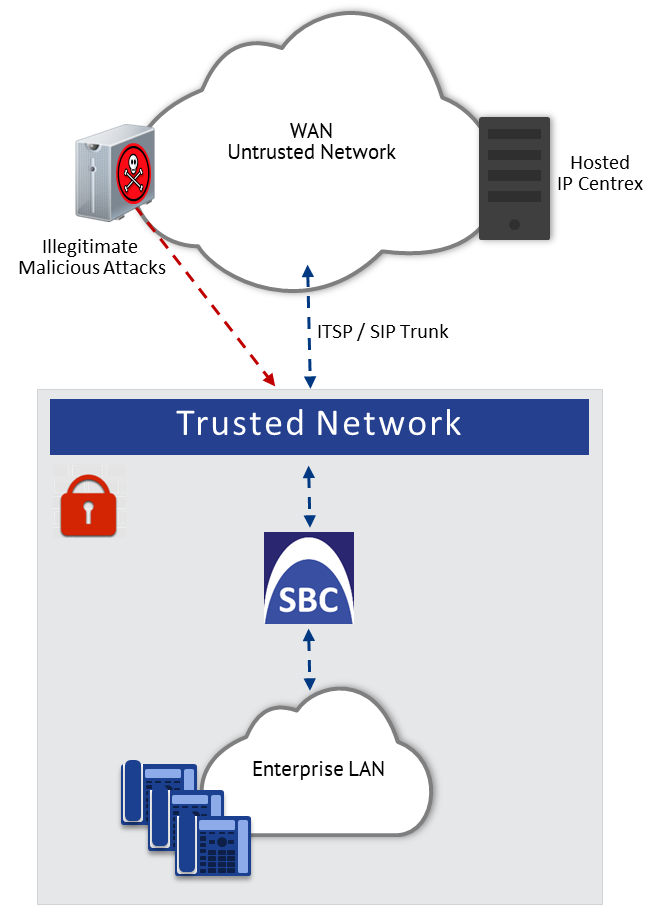
Attacks on your network from the un-trusted network may include the following:
|
■
|
Denial of Service (DoS) attacks: Malicious attacks designed to cripple your VoIP network by overloading it with calls or service requests. |
|
■
|
Overload events: In addition to purposeful DoS attacks, non-malicious periods of intense activity can also cause an increase in call signaling rates that exceed what your infrastructure can support, resulting in network conditions that are similar in effect to DoS attacks. Successful attacks resulting in contact center downtime can result in lost revenue and diminished customer satisfaction. |
|
■
|
Network abuse and fraud: Malicious intrusion or service theft may take the form of an unauthorized user gaining access to your VoIP network by mimicking an authorized user or seizing control of a SIP proxy and initiating outbound calls to the PSTN for free. Another possibility is using a compromised endpoint to redirect or forward calls for eavesdropping. |
|
■
|
Viruses and malware: Computer viruses, worms, Trojan horses, and other malware can infect user agent phones and SIP-based ACD infrastructure - just as they can computers and servers - and degrade performance or completely disrupt service. As devices become more sophisticated with distinct operating systems, malware also serves as a way to subjugate devices and launch DoS attacks that piggyback encrypted links. |
|
■
|
Identity theft: Phishing and "man-in-the-middle" can be used to acquire caller identification information to gain unauthorized access to services and information. Theft by phone (or service theft), whereby access to your corporate phone system is attempted by users posing as legitimate ones can sky-rocket your corporation's phone bill. |
|
■
|
Eavesdropping: The ability to listen to or record calls is easier on VoIP networks than on PSTN. This is a concern not only because of personal privacy violations, but also because sensitive information can be compromised and exploited. |
|
■
|
Spam over Internet Telephony (SPIT): The delivery of unsolicited calls or voicemails can inundate networks, annoy subscribers, and diminish the usefulness of VoIP networks. |
These threats can exist, for example, at the following main IP network border points:
|
■
|
Interconnect: SIP trunks to ITSPs, using SIP signaling for inbound and outbound calls. |
|
■
|
Trusted access: Private, managed IP networks that connect service providers' residential, enterprise, or mobile subscribers (as part of an emerging federation of trusted networks). |
|
■
|
Untrusted access: Unmanaged Internet for connections to work-at-home agents or inbound callers. |
