LDAP-based Login Authentication Example
To facilitate your understanding on LDAP entry data structure and how to configure the device to use and obtain information from this LDAP directory, a brief configuration example is described in this section. The example applies to LDAP-based user login authentication and authorization (access level), and assumes that you are familiar with other aspects of LDAP configuration (e.g., LDAP server's address).
The LDAP server's entry data structure schema in the example is as follows:
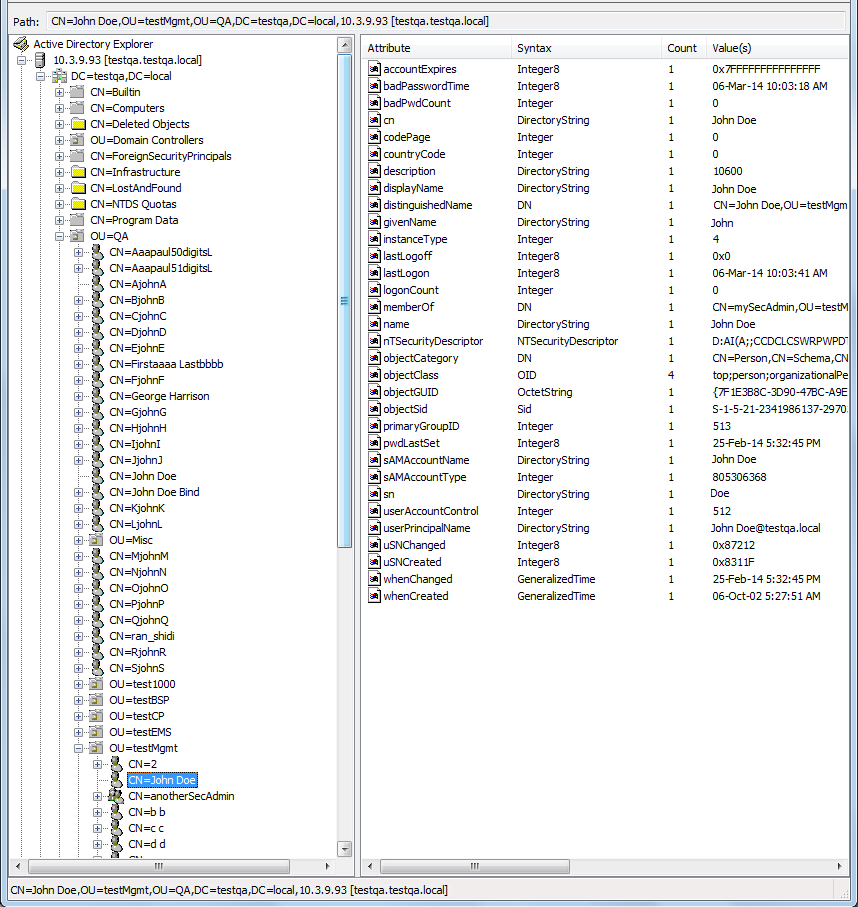
| ■ | DN (base path): OU=testMgmt,OU=QA,DC=testqa,DC=local. The DN path to search for the username in the directory is shown below: |
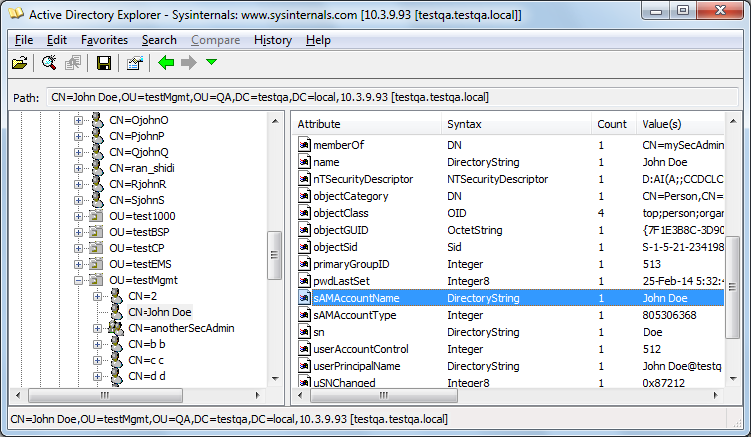
| ■ | Search Attribute Filter: (sAMAccountName=$). The login username is found based on this attribute (where the attribute's value equals the username): |
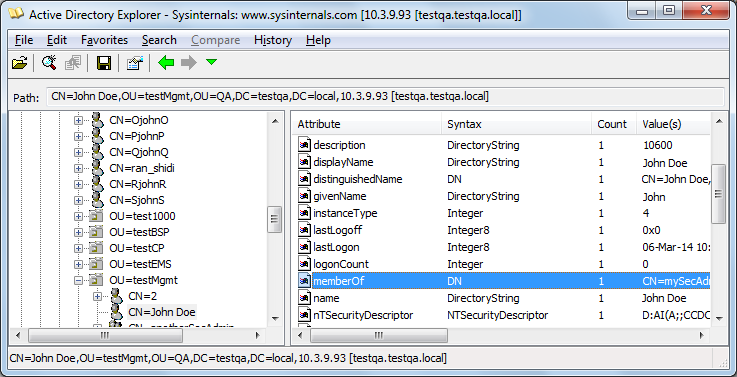
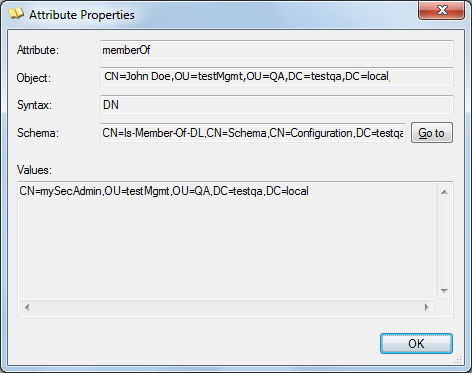
| ■ | Management Attribute: memberOf. The attribute contains the member groups of the user: |
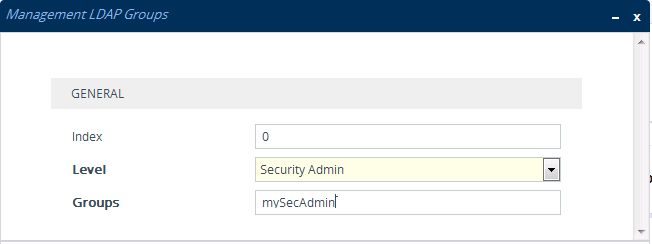
| ■ | Management Group: mySecAdmin. The group to which the user belongs, as listed under the memberOf attribute: |
The configuration to match the above LDAP data structure schema is as follows:
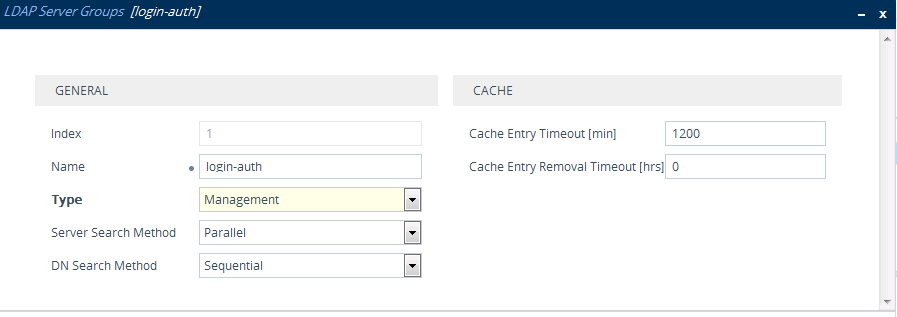
| ■ | LDAP-based login authentication (management) is enabled in the LDAP Server Groups table (see Configuring LDAP Server Groups): |
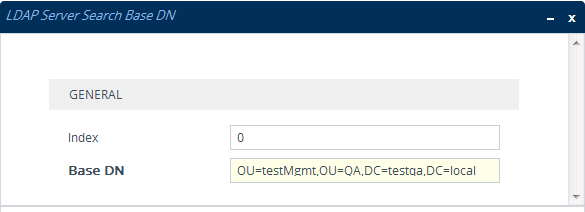
| ■ | The DN is configured in the LDAP Server Search Base DN table (see Configuring LDAP DNs (Base Paths) per LDAP Server): |
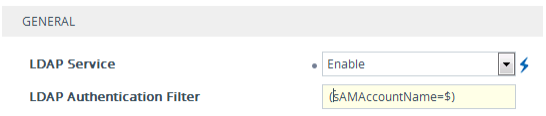
| ■ | The search attribute filter based on username is configured by the 'LDAP Authentication Filter' parameter (see Configuring the LDAP Search Filter Attribute): |
| ■ | The group management attribute is configured by the 'Management Attribute' parameter in the LDAP Servers table: |
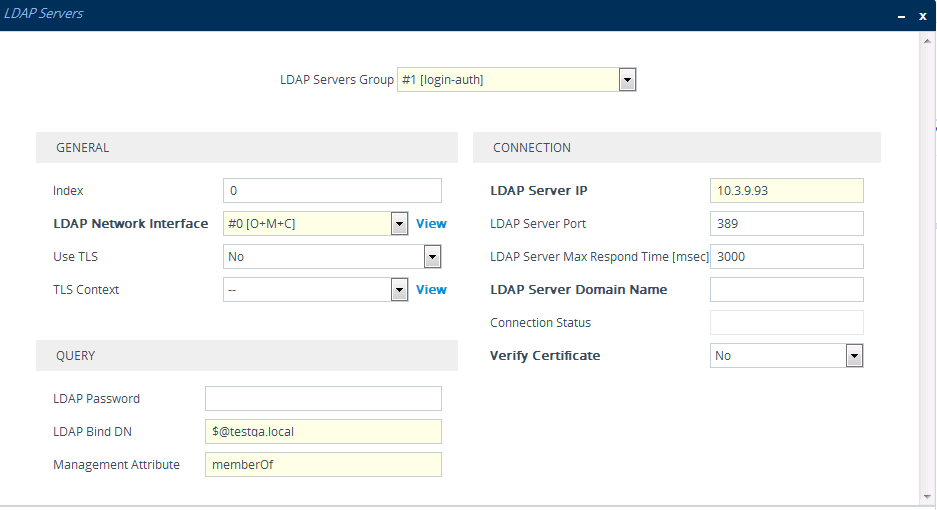
| ■ | The management group and its corresponding access level is configured in the Management LDAP Groups table (see Configuring Access Level per Management Groups Attributes): |