Viewing IDS Alarms
The device sends the following SNMP traps for the IDS feature:
| ■ | Traps that notify the detection of malicious attacks: |
| ● | acIDSPolicyAlarm: The device sends this alarm whenever a threshold of a specific IDS Policy rule is crossed. The trap displays the crossed severity threshold (Minor or Major), IDS Policy and IDS Rule, and the IDS Policy-Match index. |
| ● | acIDSThresholdCrossNotification: The device sends this event for each scope (IP address) that crosses the threshold. In addition to the crossed severity threshold (Minor or Major) of the IDS Policy-Match index, this event shows the IP address (or IP address:port) of the malicious attacker. |
If the severity level is raised, the alarm of the former severity is cleared and the device sends a new alarm with the new severity. The alarm is cleared after a user-defined timeout during which no thresholds have been crossed.
| ➢ | To configure IDS alarm cleared timeout: |
| 1. | Open the IDS General Settings page (Setup menu > Signaling & Media tab > Intrusion Detection folder > IDS General Settings). |
| 2. | From the 'IDS Alarm Clear Period' field (IDSAlarmClearPeriod), enter the timeout (in seconds) after which the alarm is cleared if no IDS thresholds have been crossed during the timeout. |
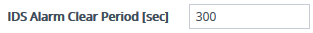
| 3. | Click Apply. |
This "quiet" timeout period must be at least twice the 'Threshold Window' value (configured in Configuring IDS Policies). For example, if you configure 'IDS Alarm Clear Period' to 20 sec and 'Threshold Window' to 15 sec, the 'IDS Alarm Clear Period' parameter is ignored and the alarm is cleared only after 30 seconds (2 x 15 sec).
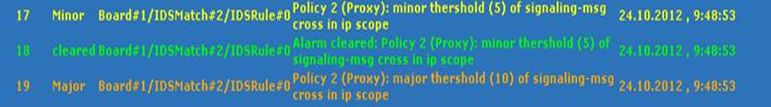
The figure below displays an example of IDS alarms in the Active Alarms table (Viewing Active Alarms). In this example, a Minor threshold alarm is cleared and replaced by a Major threshold alarm:
| ■ | acIDSBlacklistNotification event: The device sends this event whenever an attacker (remote host at IP address and/or port) is added to or removed from the blocked list. To view the IDS blocked list, see Viewing IDS Active Blocked List. |
You can also view IDS alarms through CLI:
| ■ | To view all active IDS alarms: |
# show voip ids active-alarm all
| ■ | To view all IP addresses that have crossed the threshold for an active IDS alarm: |
# show voip ids active-alarm match <IDS Match Policy ID> rule <IDS Rule ID>
The IP address is displayed only if the 'Threshold Scope' parameter is set to IP or IP+Port; otherwise, only the alarm is displayed.
The device also sends IDS notifications and alarms in syslog messages to a syslog server. This occurs only if you have configured syslog (see Enabling Syslog). An example of a syslog message with IDS alarms and notifications is shown below:
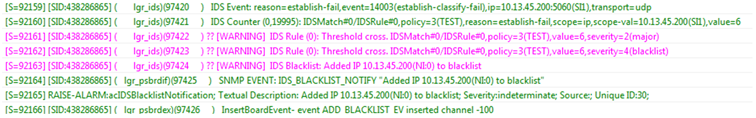
The table below lists the syslog text messages per malicious event:
Types of Malicious Events and Syslog Text String
|
Reason |
|
|---|---|
|
Description |
Syslog String |
|
Connection Abuse |
|
|
TLS authentication failure |
abuse-tls-auth-fail |
|
WebSocket establishment failure |
abuse-websocket-fail |
|
Malformed Messages |
|
|
Message exceeds a user-defined maximum message length (50K) |
malformed-invalid-msg-len |
|
Any SIP parser error |
malformed-parse-error |
|
Message policy match |
malformed-message-policy |
|
Basic headers not present |
malformed-miss-header |
|
Content length header not present (for TCP) |
malformed-miss-content-len |
|
Header overflow |
malformed-header-overflow |
|
Authentication Failure |
|
|
Local authentication ("Bad digest" errors) |
auth-establish-fail |
|
Remote authentication (SIP 401/407 is sent if original message includes authentication) |
auth-reject-response |
|
Dialog Establishment Failure |
|
|
Classification failure |
establish-classify-fail |
|
Routing failure (no matched routing rule) |
establish-route-fail |
|
Other local rejects (prior to SIP 180 response) |
establish-local-reject |
|
Remote rejects (prior to SIP 180 response) |
establish-remote-reject |
|
Malicious signature pattern detected |
establish-malicious-signature-db-reject |
|
CAC threshold exceeded |
establish-cac-reject |
|
Abnormal Flow |
|
|
Requests and responses without a matching transaction user (except ACK requests) |
flow-no-match-tu |
|
Requests and responses without a matching transaction (except ACK requests) |
flow-no-match-transaction |