Define Malicious Signatures
To protect the device from malicious attacks on SBC calls, it's recommended to employ the device's Malicious Signature feature, which defines malicious signature patterns. The Malicious Signature feature identifies and protects against SIP (Layer 5) threats by examining new inbound SIP dialog messages. Once the device identifies an attack based on the configured malicious signature patterns, it marks the SIP message as invalid and discards it (or alternatively, rejects it with a SIP response). Malicious signatures are typically based on the SIP User-Agent header, which attackers often use as their identification string (e.g., "User-Agent: VaxSIPUserAgent").
| ➢ | To configure malicious signatures: |
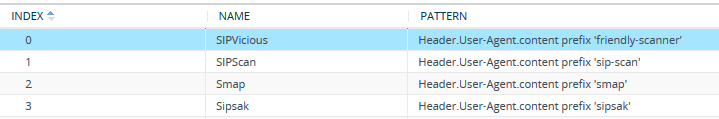
| 1. | Open the Malicious Signature table (Setup menu > Signaling & Media tab > SBC folder > Malicious Signature), and then configure malicious signatures. The device provides preconfigured malicious signatures. |
Configuring Malicious Signatures
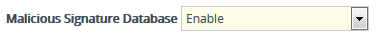
| 2. | Open the Message Policies table (Setup menu > Signaling & Media tab > Message Manipulation folder > Message Policies), and then configure a Message Policy and enable it to use the malicious signatures, by configuring 'Malicious Signature Database' to Enable: |
Enabling Malicious Signatures for Message Policy
| 3. | Open the SIP Interfaces table (Setup menu > Signaling & Media tab > Core Entities folder > SIP Interfaces). |
| 4. | For the SIP Interface of the calls that you want to apply the malicious signatures policy, from the 'Message Policy' drop-down list, select the Message Policy that you configured in Step 1: |
Assigning Message Policy to SIP Interface
